The Internet has become an indispensable part of modern life. We use networks for work, study, entertainment, financial transactions, and even storing personal information. But alongside these conveniences, the internet also carries many risks: from hackers stealing data, ads tracking user behavior, to access restrictions in many countries.
In that context, VPN (Virtual Private Network) emerged as a solution that not only helps protect personal information but also provides the freedom to access content on the internet. VPN is no longer an unfamiliar concept, but many people still do not fully understand how it works, its benefits, and the risks of using it.
This article will help you gain a deeper understanding of VPNs: from the concept, operating mechanism, and practical benefits to how to choose the right service and future trends.

1. What is a VPN?
VPN (Virtual Private Network), also known as a virtual private network, is a technology that allows users to create a secure “tun
Simply put, imagine the internet as a public highway where anyone can see where your car is going. A VPN is like a private underground tunnel: only you and your destination know the journey, while outsiders cannot observe it.
How is VPN different from Proxy and Tor?
- VPN khác gì so với Proxy và Tor?
- Tor provides a high level of anonymity by routing data through multiple intermediary nodes, but the speed is often slow.
- VPN strikes a balance between security, speed, and usability, making it suitable for most regular users and businesses.
2. How does a VPN work?
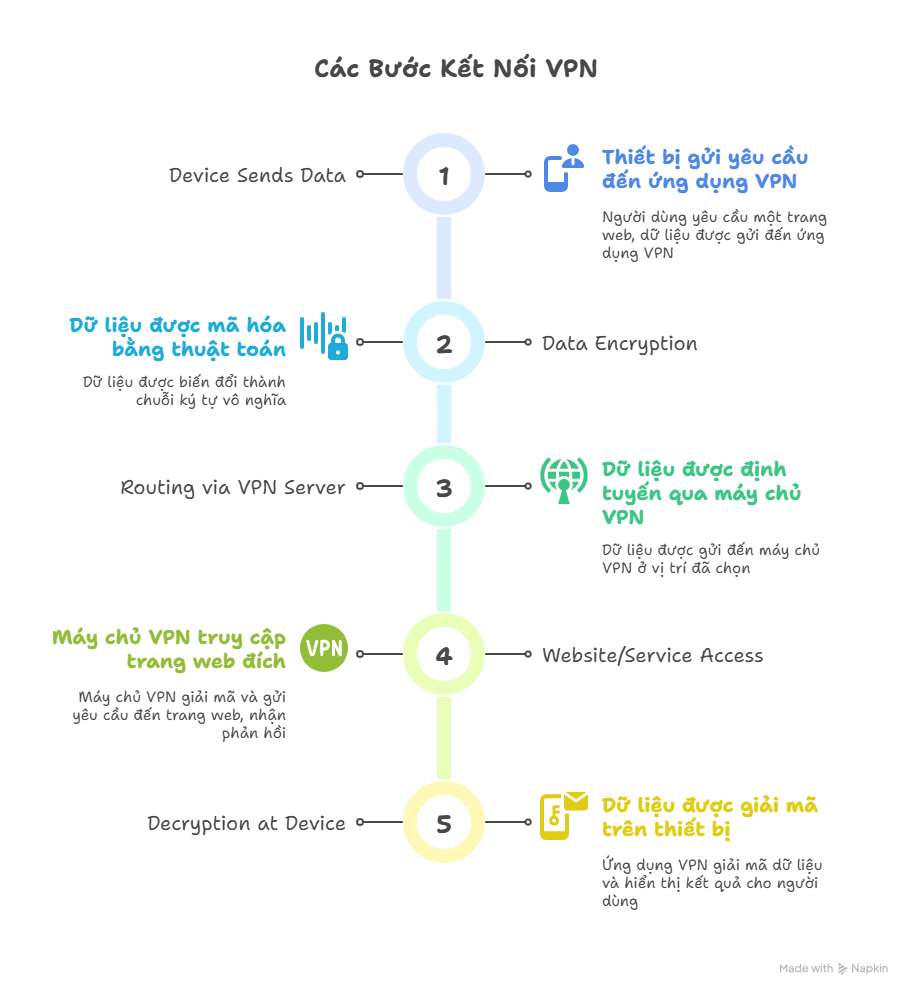
When you turn on a VPN, the entire process of connecting to the internet changes. Instead of connecting directly to a website/service, your data goes through a private “tunnel” and is encrypted. This process is basically carried out through the following steps:
1. The device sends data
- For example: you want to access
www.kienthucmo.com. Normally, the device would send the request directly to kienthucmo.com - But when the VPN is enabled, that request is first sent to the VPN application on the device.
2. Data encryption
- A VPN uses encryption algorithms (AES-256, ChaCha20, etc.) to transform data into a “string of meaningless characters.”
- If someone intercepts the data (for example, a hacker on public Wi-Fi), they will only see garbled code and cannot read the content.
- This is why a VPN is often compared to “packing data inside a locked box.”
3. Routing through the VPN server
- After being encrypted, the data is sent to a VPN server at the location you choose (for example: the US, Japan, or Singapore).
- This server acts as an intermediary, communicating with the internet on your behalf.
4. Accessing the website/service
- The VPN server decrypts the necessary data and then forwards the request to the destination website (for example, kienthucmo.com).
- The website will “think” the request is coming from the VPN server, not from your actual device.
- After that, the response (the website content) is sent back to the VPN server → re-encrypted → and then delivered to your device.
5. Decryption on the device
- The VPN application on your device decrypts the received data and displays the final result (website, video, email, etc.).
Simple example
- Without VPN: You send a letter directly through the post office. Others can see the envelope, the sender’s address, and if it is not sealed properly, they may even read the content.
- With VPN: You put the letter inside a locked metal box and give it to a trusted friend (the VPN server). Outsiders only see you handing the box to that friend, but they do not know what’s inside or who you intend to send it to. Your friend then delivers the letter to the recipient on your behalf.
3. Common VPN Protocols
| Protocol | Security | Speed | Stability | Main Use Cases |
|---|---|---|---|---|
| PPTP | Low | Very Fast | High | Unblocking content, not recommended for security |
| L2TP/IPSec | Medium | Medium | Medium | Basic connections, PPTP replacement |
| OpenVPN | Very High | Good | High | Current standard, versatile |
| IKEv2/IPSec | High | Fast | Very High | Mobile devices, flexible connections |
| WireGuard | Very High | Very Fast | High | The future of VPN, adopted by many new services |
4. Benefits of Using a VPN
4.1. Security and Data Protection
When you connect at a café, airport, or hotel, public Wi-Fi is often unsafe. Hackers can intercept data to steal passwords, emails, or banking information. A VPN encrypts the data, making it unreadable even if intercepted.
4.2. Privacy and Anonymity
A VPN helps you hide your real IP address. Internet service providers (ISPs) or advertisers will not know exactly what you are accessing. This is especially important in a context where personal data is often collected for advertising purposes.
4.3. Accessing restricted content
Many services restrict content based on the country. For example, Netflix US has a different movie library than Netflix Vietnam. A VPN allows you to “spoof” your IP to the US to access that library. Similarly, you can watch BBC iPlayer in the UK or access YouTube in regions where it is blocked.
4.4. Supporting Remote Work
For businesses, a VPN allows employees to securely access internal systems while working from home or traveling. This is an essential solution in the era of booming remote work.
4.5. Other Practical Applications
- Gamers: reduce ping when connecting to international servers, or bypass regional restrictions.
- Journalists and activists: protect identity and avoid surveillance in areas with strict censorship.

5. Limitations and Risks of Using a VPN
A VPN is not always perfect. Users need to consider the following points:
- Slow speed: because data must be encrypted and routed through an intermediary server.
- Some services block VPNs: For example, Netflix frequently updates to prevent VPN access.
- Free VPNs: may sell data, insert ads, or have weak security.
- Not all VPNs are “no-log”: some providers still keep a record of your activity.
6. Types of VPNs Today
- Personal VPN
- Target users: General users.
- Purpose:
- Hide IP address, encrypt data while browsing the web.
- Avoid tracking by ISPs, hackers, or advertisers.
- Unblock region-restricted content (for example: watch Netflix US while in Vietnam).
- Advantages: Easy to implement, low cost, many options available on the market.
- Disadvantages: Primarily serves personal needs, not powerful enough for enterprise use.
- Target users: General users.
- Corporate VPN
- Users: Businesses, organizations.
- Purpose:
- Securing employee access to internal data (intranet, company servers).
- Managing access rights and assigning permissions to employees.
- Facilitates secure connections for remote work.
- Securing employee access to internal data (intranet, company servers).
- Advantages: Centralized control, data security.
- Disadvantages: High deployment cost, requires IT team management.
- Users: Businesses, organizations.
- Remote Access VPN
- Users: Individuals in a company who need to work remotely.
- How it works: The user installs the VPN application → enters login credentials → connects to the company network via the Internet.
- Practical application: Employees on business trips can still access the company’s file server and ERP/CRM systems.
- Advantages: Flexible, easy to deploy for individual employees.
- Disadvantages: If too many people connect remotely at the same time, it may slow down the system.
- Users: Individuals in a company who need to work remotely.
- Site-to-Site VPN
- Users: Businesses with multiple offices/branches.
- How it works: Connects the LANs of each branch via VPN, creating a unified network system.
- Practical application:
- A company with headquarters in Hanoi and a branch in Ho Chi Minh City → Site-to-Site VPN allows both offices to access internal data as if they were on the same network.
- Useful for banks, large corporations, and retail chains.
- Advantages: Ensures synchronization and data security across branches.
- Disadvantages: Complex configuration, requires specialized hardware (router, firewall).
- Users: Businesses with multiple offices/branches.
7. Criteria for Choosing the Right VPN
- No-Log Policy
This is a top priority criterion. A reliable VPN service must commit to not recording users’ access history. If the provider keeps logs, your personal data could be sold or shared with third parties. - Diverse Servers in Multiple Countries
The more servers a VPN has worldwide, the easier it is for users to optimize speed and access region-restricted content. For example, you can connect to a US server to watch Netflix US, or a Japan server to play games in that region. - Stable Speed
Since data must be encrypted and routed through an intermediary server, speed is an important consideration. A good VPN should provide fast enough speeds for web browsing, remote work, HD video streaming, or even gaming without lag. - Support for Strong Security Protocols
Protocols are the “backbone” of a VPN. Modern protocols like OpenVPN, IKEv2/IPSec, or WireGuard provide a balance between speed and security. In contrast, older protocols like PPTP are no longer safe to use. - Responsive Customer Support
A reputable provider should offer 24/7 support via chat or email. This is especially useful when users encounter difficulties connecting or setting up the VPN on multiple devices. - Reasonable Pricing
The most expensive VPN is not necessarily the best for you. Individual users can choose affordable plans with sufficient features, while businesses should invest in premium plans for security and centralized management. Additionally, many providers offer discounts for long-term subscriptions.
8. Conclusion
VPN is not just a technical tool for IT professionals; it has become a popular solution that helps everyone protect personal information, maintain privacy, and freely access the internet.
However, a VPN is not an “invincible shield.” Users still need to be cautious by choosing reputable services and avoiding low-quality free VPNs.
If you want to be safer online, secure your information while working remotely, or simply access global content, a VPN is definitely a choice worth considering.