In today’s technology – driven world, cybersecurity is no longer an unfamiliar issue. Every time we connect to the Internet, send an email, or access a website, there are always potential risks – from unauthorized intrusions to attacks on personal data. This is precisely why a Firewall has become one of the most critical layers of defense in any network system.
When I first began learning about it, I thought a firewall was simply software that blocked viruses or suspicious websites. However, the deeper I explored, the more I realized that it is an intelligent mechanism, functioning like a true “gatekeeper” – constantly monitoring, analyzing, and deciding which data packets are allowed to pass through the system.
In this article, I will explore with you everything from the fundamental concept and operating principles to modern firewall types and future trends. Hopefully, this piece will provide you with a more comprehensive perspective on one of the most important components of network security.
1. Concept and Role of a Firewall
1.1 Concept of a Firewall
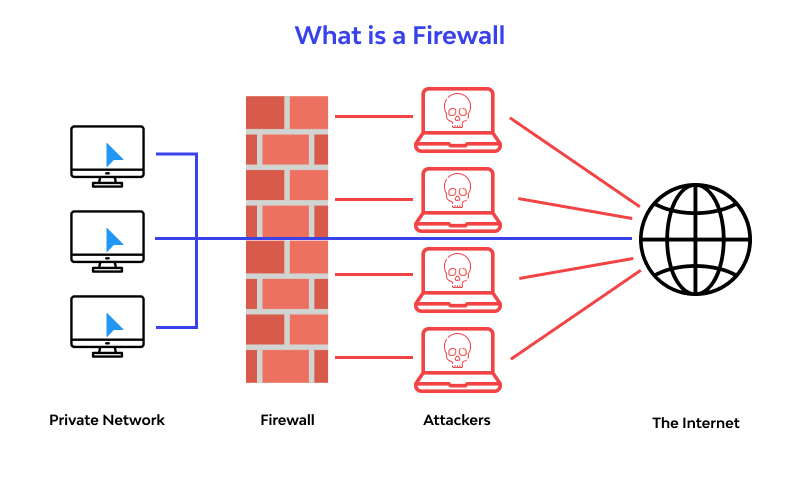
A Firewall – also known as a “network firewall” – is a security system designed to monitor, filter, and control network traffic entering or leaving between two or more different network zones. Typically, it is positioned between an internal network—where critical resources are stored – and the Internet, which poses numerous security risks.
In simple terms, a firewall functions like a security checkpoint at the entrance of a building. Every “visitor” – that is, each data packet – must undergo inspection and identity verification. If deemed legitimate, it is allowed to pass; if suspicious or non-compliant with established rules, it is immediately blocked.
1.2 Role of a Firewall
A firewall plays a vital role in ensuring network security. Below are the core responsibilities commonly performed by a firewall:
- Access Control: A firewall determines who is permitted to access the system and who is denied, based on predefined rules. These rules may rely on IP addresses, ports, protocols, or even the content of data packets.
- Unauthorized Access Prevention: Acting as the first line of defense, a firewall helps prevent hackers, malware, and remote attacks from infiltrating the internal network. As a result, it significantly reduces the risk of data breaches or system compromise.
- Network Monitoring and Logging: All traffic passing between network zones is recorded in log files by the firewall. This information enables network administrators to detect abnormal behavior, trace incidents, and assess the overall security posture of the system.
Today, firewalls can be integrated into routers, deployed on enterprise servers, or installed as personal security software on individual computers. Regardless of scale – large or small – the core functions of a firewall remain fundamentally the same.
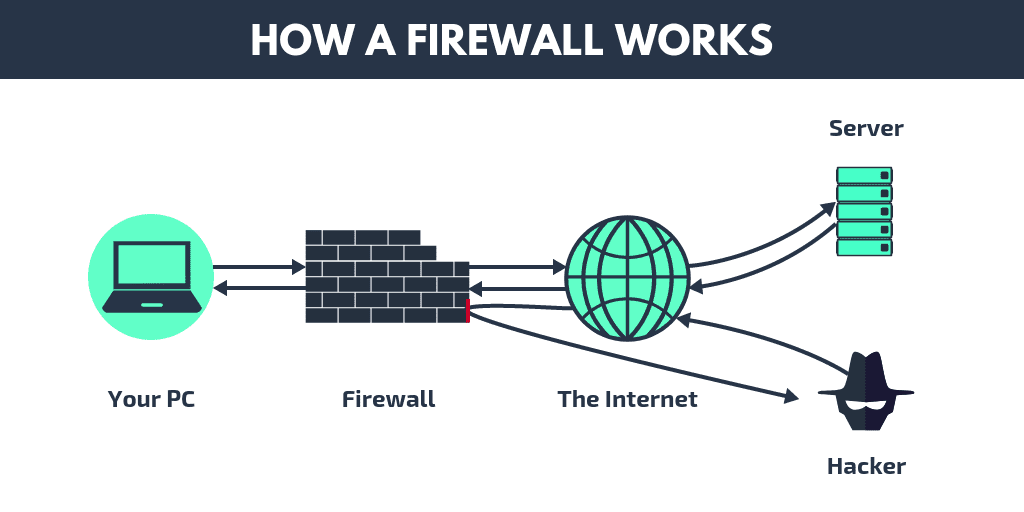
2. How a Firewall Works
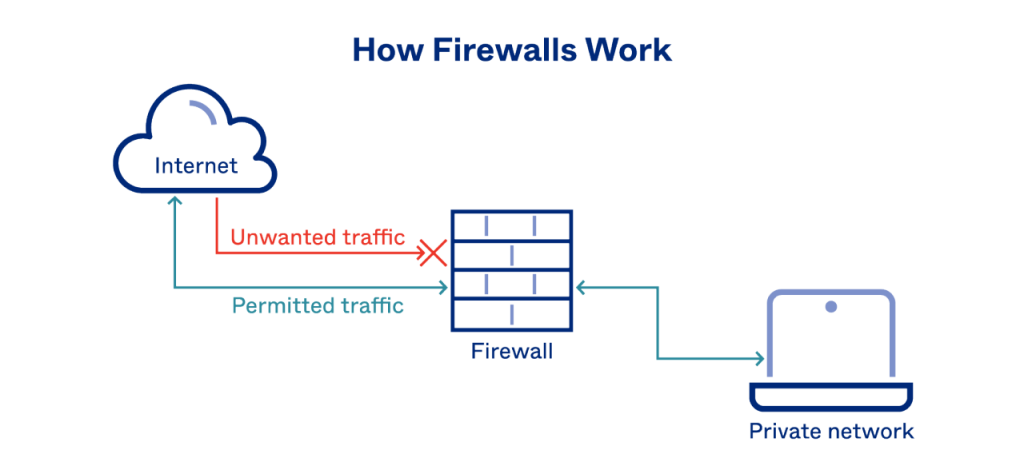
From a technical perspective, a Firewall analyzes network traffic through packet inspection and makes decisions based on predefined security policies. Several common operating mechanisms are outlined below:
Packet Filtering: This method examines packet headers—such as source and destination IP addresses, ports, and protocols—and compares them against a rule set. It is a basic and fast approach, but limited because it does not track connection states or inspect application-level content.
Stateful Inspection: With this approach, the firewall keeps track of the state of active connections (e.g., TCP handshakes and session tables). Once a packet is recognized as part of a legitimate session, it is allowed through without being re-evaluated each time. This makes stateful inspection more intelligent and secure than simple packet filtering.
Proxy / Application-Level Gateway: Operating as an intermediary for applications (for example, an HTTP proxy), this mechanism has deep awareness of protocol contents. It can filter traffic based on URLs, headers, and even message content, making it suitable for environments that require fine-grained application control.
Next-Generation Firewall (NGFW): NGFWs combine traditional firewall capabilities with advanced features such as application identification, user-based control, integrated IDS/IPS, anti-malware protection, and often the use of threat intelligence or machine learning to detect malicious behavior. Rather than relying solely on ports and protocols, NGFWs analyze traffic at the application layer to provide enhanced security.
3. Firewall Classification
Firewalls can be classified in multiple ways depending on their deployment model and protective functions. Understanding each type helps organizations select a solution that aligns with their system scale and security objectives.
3.1 By Deployment Location
Network-based Firewall (appliance / virtual): Deployed at the network perimeter or between network segments to filter traffic for multiple hosts. This model is well suited for enterprise environments due to its ability to handle high traffic volumes and centralized management; however, it typically involves higher costs and operational complexity.
Host-based Firewall (software): Runs directly on individual machines (for example, Windows Firewall or ufw). It provides fine-grained, host-level control and is relatively low-cost, but requires automation and careful management when deployed across a large number of systems.
3.2 By Filtering Method / Functionality
Packet-Filtering Firewall (stateless): Inspects packet headers such as IP addresses, ports, and protocols. It is fast and simple, but does not track connection states or inspect payload content.
Circuit-Level Gateway: Validates sessions (for example, through the TCP handshake) and then opens a “circuit” for data transmission. It ensures that connections are legitimate but does not examine the actual data payload.
Application-Level Gateway (Proxy): Operates at the application layer, analyzing headers and content, and supporting URL filtering and authentication. While it offers deep control, it is resource-intensive and may introduce latency.
Stateful Firewall: Tracks the state of connections (e.g., NEW / ESTABLISHED / RELATED). It provides stronger security than stateless packet filtering but requires memory to maintain state tables.
Next-Generation Firewall (NGFW): Provides application awareness, user-based control, and integrates features such as IDS/IPS and threat intelligence feeds. While highly effective, NGFWs are more complex to deploy and operate, and typically involve higher costs.
4. Advantages and Limitations of Firewalls
A Firewall serves as a critical protective layer in a network security architecture, helping control traffic and prevent unauthorized access. However, like any security tool, it has inherent limitations.
- Advantages:
One of the greatest strengths of a firewall is its ability to block unauthorized external access, protecting systems from hackers and malware. Firewalls also support bandwidth management and content filtering, enabling organizations to control the types of data allowed to traverse the network – for example, blocking access to unsafe websites. In addition, security policies are relatively straightforward to configure, allowing administrators to quickly adjust rules to meet operational requirements.
- Limitations:
Despite their strength, firewalls cannot protect against threats originating from within the system, such as intentional data leakage by employees or accidental downloads of malicious software. Misconfiguration can also degrade network performance, causing access delays and negatively affecting user experience. Moreover, a firewall cannot fully replace other security measures such as intrusion detection systems (IDS), data encryption, or employee security awareness training.
In essence, a firewall is only one component of a “defense-in-depth” cybersecurity strategy. To achieve maximum effectiveness, it must be combined with complementary solutions such as antivirus software, IDS/IPS, user behavior monitoring, and regular system updates. Only then can an organization build a truly resilient defense against evolving cyber threats.
5. Real-World Applications of Firewalls
A Firewall is present in nearly every technology environment—from enterprises and households to cloud platforms—serving as the first line of defense against cyber threats.
In enterprise environments: Firewalls protect internal systems, segment DMZ zones, and restrict direct access to administrative servers. Organizations commonly deploy Next-Generation Firewalls (NGFWs) to identify applications, users, and anomalous behavior. This approach not only prevents unauthorized access but also enables early detection of sophisticated attacks such as malware infections or stealthy intrusions.
For home users: Most modern routers come with built-in basic firewall capabilities, which are sufficient to block unwanted access and manage IoT devices. Users can also leverage firewalls to filter inappropriate content or limit Internet access for children, thereby improving overall home network safety.
In cloud environments: Cloud providers such as Amazon Web Services (AWS) and Microsoft Azure offer virtual firewalls in the form of “Security Groups.” These function as virtual barriers protecting resources (for example, EC2 instances), allowing flexible configuration of inbound and outbound rules. This represents a critical security layer in cloud infrastructure, where traditional on-premises physical devices no longer exist.
6. The Future of Firewalls
A Firewall is undergoing a significant transformation—from simple port- and IP-based filtering toward deeper analysis of applications, users, and behavior. The objective is to deliver protection that is more flexible, intelligent, and suited to increasingly complex network environments.
A prominent trend today is the evolution of Next-Generation Firewalls (NGFWs) combined with AI and machine learning, enabling automated detection of anomalous behavior and more effective threat classification. Vendors such as Palo Alto Networks have already adopted these technologies to improve accuracy while reducing false positives.
In parallel, the Firewall-as-a-Service (FWaaS) model is gaining traction, allowing organizations to deploy and manage firewalls directly from the cloud. This approach is particularly well suited to hybrid and multi-cloud environments.
Additionally, Zero Trust and microsegmentation are becoming inevitable directions. Modern firewalls now support fine-grained policies for individual users and workloads, ensuring tighter internal access control across systems.
In my view, firewalls will continue to play a core role in the future, but with deeper integration into automation, threat intelligence, and user management—making security smarter and more adaptive to emerging threats.
7. Conclusion
A Firewall is one of the most critical foundations of modern cybersecurity, enabling access control, network segmentation, and activity logging for monitoring and incident investigation. However, a firewall alone is not a complete shield capable of protecting an entire system.
To achieve a truly robust security posture, firewalls must be combined with multiple additional layers, such as regular software updates, endpoint protection, IDS/IPS deployment, backup and recovery policies, and user security awareness training. Only when these elements operate in concert can an organization effectively withstand increasingly sophisticated cyber threats.
8 References
[1] Cisco, “What Is a Firewall?,” Cisco.com. [Online]. Available: Cisco Learn. Truy cập: 2025.
[2] Palo Alto Networks, “What Is a Next-Generation Firewall (NGFW)?,” PaloAltoNetworks.com. Truy cập: 2025.
[3] Amazon Web Services, “Control traffic to your AWS resources using security groups,” AWS Documentation. Truy cập: 2025.
[4] R. Presuhn, “RFC 2979 — Behavior of and Requirements for Internet Firewalls,” IETF, Oct. 2000. Available: IETF Datatracker.
[5] W. Stallings, Network Security Essentials: Applications and Standards, 6th ed., Pearson, 2023.