Security is not solely the responsibility of the cybersecurity team. In reality, just a small mistake in the source code — a control point that isn’t strict enough, a statement that hasn’t been properly sanitized — can be enough for an attacker to exploit and cause serious damage to the entire system. Therefore, identifying and preventing vulnerabilities right from the design and web application development stages is something that cannot be overlooked.
In order to support developers, testers, and technical professionals in approaching security in a more systematic and effective way, the OWASP organization was founded. With the mission of raising awareness and providing open-source standards for web application security, OWASP has become one of the most reputable and widely trusted platforms worldwide.
Let’s take a closer look at what OWASP is, the value this organization brings to the software development community, and why the OWASP Top 10 documentation has become an essential foundation for building secure web applications. Understanding these core concepts not only helps you avoid common security mistakes but also equips you with practical knowledge to handle increasingly sophisticated cyber threats today.

1. What is OWASP?
OWASP (short for Open Web Application Security Project) is an international nonprofit organization specializing in web application security. Sounds a bit “academic,” but simply put, OWASP is an open community — a place where security experts, software engineers, and researchers share knowledge, tools, and resources to help developers write safer code and protect applications from common vulnerabilities.
“
What makes OWASP special is that all of its documents and tools are free and publicly available. Anyone — whether a student, developer, or security professional — can access, learn, and apply them in real-world projects.
1.1 Some of OWASP’s Notable Projects
- OWASP Top 10
A list of the 10 most common security vulnerabilities in web applications, updated periodically based on global data. This serves as a reference standard to help developers and security professionals identify, prioritize, and address critical risks.
- OWASP ZAP (Zed Attack Proxy)
An open-source security testing tool used to detect vulnerabilities in websites. ZAP functions as an intermediary proxy and supports both automated and manual testing, making it suitable for integration into DevSecOps workflows.
- OWASP Cheat Sheet Series
A collection of concise and easy-to-understand guides that help developers write more secure code. Each cheat sheet focuses on a specific topic such as authentication, encryption, or API security, making it highly useful for everyday security practices.
- OWASP ASVS (Application Security Verification Standard)
Bộ tiêu chuẩn giúp xác minh và đánh giá mức độ an toàn của ứng dụng, cung cấp khung kiểm thử rõ ràng cho các doanh nghiệp và đội phát triển phần mềm.
- OWASP Dependency-Check
A tool that detects vulnerabilities in third-party libraries and dependencies, helping ensure that applications are not affected by insecure components.
- OWASP Web Security Testing Guide (WSTG)
A comprehensive web security testing guide that includes methodologies, techniques, and test cases for various types of vulnerabilities.
1.2 Why Is OWASP Important to You?
If you are a developer, OWASP is like a reliable companion — always reminding you of common mistakes, pointing out potential risks, and more importantly, helping you write code that not only works well but is also safe for users. After all, there’s nothing worse than having the application you built become a gateway for attackers to harm others.
And if you are an everyday user, you might not even know what OWASP is — but thanks to the standards set by OWASP, the things you do every day such as online shopping, logging into your bank account, or simply reading news on a website are silently being protected in the background. OWASP may not be visible in the user interface, but it helps make the digital world you live in a little safer every day.
The importance is clear — next, let’s go over the 10 most common vulnerabilities today so we can understand their mechanisms and how to remediate them. Let’s get started…!!!
2. OWASP Top 10 – The most common security vulnerabilities list

OWASP Top 10 is a document that summarizes the ten most common and critical security vulnerabilities in web applications, updated periodically based on real-world data from hundreds of security organizations. OWASP Top 10 is not just a list — it is a wake-up call for anyone working with the web, from backend developers to testers, sysadmins, and security researchers. Below, we will dive into each vulnerability, explain how it works, its real-world impact, and sustainable prevention methods.
The latest OWASP Top 10 version (2021) includes:
2.1 Injection (SQL Injection, Command Injection…)
Risk: Attackers inject malicious SQL statements into input fields such as search boxes or login forms. For example, entering ' OR 1=1 -- into a password field can bypass authentication and grant unauthorized access.
Impact: Attackers can read, modify, or delete sensitive data in the database.
Prevention: Use ORM (Object-Relational Mapping) tools like Django ORM instead of writing raw SQL queries. Use prepared statements or parameterized queries. Validate, sanitize, and reject invalid user input.
2.2 Cross-Site Scripting (XSS)
Risk: Attackers inject malicious JavaScript code into comments, forms, or URLs. When other users visit the page, the script executes and steals cookies, login credentials, etc.
Impact: User accounts may be hijacked; the website may be defaced or injected with malicious content.
Prevention: Encode all output before rendering to HTML. Do not allow users to insert HTML/JS code (or use a strict whitelist if necessary). Implement Content Security Policy (CSP) to restrict executable scripts.
2.3 Broken Authentication
Risk: Credential stuffing (using leaked usernames/passwords to log in automatically) or brute-force attacks (trying numerous random passwords).
Impact: Hackers can gain access to user or administrator accounts.
Prevention: Use strong password hashing (bcrypt, argon2). Implement login attempt limits, CAPTCHA, and two-factor authentication (2FA). Always regenerate session IDs after login.
2.4 Insecure Deserialization
Risk: Attackers send serialized data containing malicious code. When the system deserializes it without proper validation, the malicious code gets executed.
Impact: Attackers may achieve Remote Code Execution (RCE).
Prevention: Avoid deserializing data received from clients unless it has been strictly validated. Use safer data formats such as JSON instead of binary formats or pickle. Apply digital signatures or encryption to verify data integrity.
2.5 Sensitive Data Exposure
Risk: Attackers steal data because the system stores or transmits information without encryption (e.g., using HTTP instead of HTTPS, storing passwords in plain text).
Impact: Leakage of personal, financial, or user password information.
Prevention: Always use HTTPS (TLS) to encrypt connections. Passwords must be hashed with strong salting. Do not log sensitive information to console or files.
2.6 Security Misconfiguration
Risk: Attackers exploit leaked sensitive information such as detailed error messages, .env files, or unprotected admin pages.
Impact: Attackers may discover weaknesses that allow them to take control of the system.
Prevention: Disable debug mode in production environments. Restrict access to critical files. Enforce strict authentication for admin pages and APIs.
2.7 Broken Access Control
Risk: Attackers modify URLs or requests to access resources that do not belong to them. For example:
/user/123/edit -> /user/124/edit.
Impact: Unauthorized access to data or manipulation of the system.
Prevention: Enforce access control on the server side (not just the frontend). Revalidate user roles and permissions on every request. Never trust client-side data.
2.8 Directory Traversal / File Upload Vulnerabilities
Risk: Attackers rename an uploaded file to ../../../etc/passwd to access system files, or upload a shell script to gain control of the server.
Impact: Attackers can access or take over the server.
Prevention: Restrict allowed file types for upload. Rename stored files to prevent execution. Validate the real MIME type and file extension. Do not allow direct access to the upload directory.
2.9 Security Logging and Monitoring Failures
Risk: The system does not record logs or lacks early alerts during attacks (SQLi, XSS, brute-force, etc.).
Impact: Attackers can silently exploit the system over a long period without being detected.
Prevention: Enable comprehensive and detailed logging, protect logs from unauthorized access, integrate monitoring systems (SIEM), enable real-time alerts, and perform regular log audits.
2.10 Server-Side Request Forgery (SSRF)
Risk: Attackers exploit features like image preview from a URL to trick the server into accessing internal resources (e.g., http://127.0.0.1:8080/admin).
Impact: Unauthorized access to internal resources or gaining control of the server.
Prevention: Restrict allowed destination URLs, block access to internal IP addresses, use firewalls or internal proxies, and regularly update third-party libraries.
3. Practical Application of OWASP in Software Development
OWASP is not just a list of vulnerabilities – it is a guideline for building secure, sustainable, and reliable software. Applying OWASP resources and recommendations at every stage of software development can significantly reduce security risks and help ensure compliance with international standards.

3.1 Applying OWASP in the Software Development Phase
| Phase | Applying OWASP |
| Requirements & Analysis | Use OWASP ASVS (Application Security Verification Standard) to define security requirements from the outset. |
| Design | Apply OWASP Threat Modeling to analyze threats and design systems to defend against them. |
| Programming | Follow OWASP Secure Coding Practices to prevent vulnerabilities such as SQL Injection, XSS, and more. |
| Testing | Use OWASP ZAP (Zed Attack Proxy) to perform both automated and manual application security testing. |
| Deployment | Follow the hardening steps in the OWASP Deployment Guide to secure the production environment. |
| Maintenance | Monitor vulnerabilities using OWASP Dependency-Check and update software regularly. |
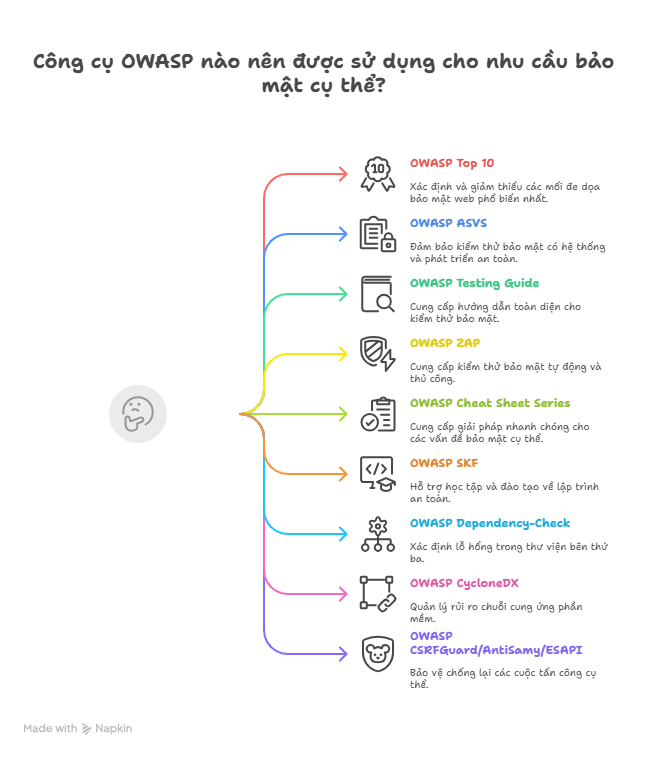
3.2 Practical OWASP Tools and Their Applications
| Resources | Description | Application |
| OWASP Top 10 | OWASP’s most prominent document, listing the 10 most common security threats to web applications. | Used by businesses, developers, and security professionals as a standard for security testing and training. |
| OWASP ASVS (Application Security Verification Standard) | A set of security assessment standards at multiple levels, designed for web applications and APIs. | Useful for guiding systematic security testing, especially when developing software with a Security by Design approach. |
| OWASP Testing Guide | A comprehensive guide on how to perform web application security testing. | An essential reference for pentesters and QA professionals who want to integrate security testing into the development process. |
| OWASP ZAP (Zed Attack Proxy) | An open-source tool for both automated and manual security testing. | Easy to use, free, and suitable for both beginners and experts. ZAP can be integrated into CI/CD pipelines for automated security testing. |
| OWASP Cheat Sheet Series | A concise, practical guide covering specific security topics such as Authentication, Session Management, HTTPS Configuration, SQL Injection, and more. | Short and easy to understand, ideal for quickly finding standardized solutions to security issues. |
| OWASP Security Knowledge Framework (SKF) | A learning platform that provides secure coding guidance with practical examples. | Highly suitable for internal training, security staff education, or learning secure coding practices. |
| OWASP Dependency-Check | A tool for checking third-party libraries for known security vulnerabilities. | Very useful when using popular packages like npm, pip, Maven, etc., and wanting to ensure they have no known vulnerabilities. |
| OWASP CycloneDX | A standard format for creating an SBOM (Software Bill of Materials – a list of software components). | Used in DevSecOps to manage software supply chain risks. |
| OWASP CSRFGuard / AntiSamy / ESAPI | Libraries that help protect applications against specific attack types such as CSRF, XSS, and Injection. | Easy to integrate into Java applications and ready to use immediately. |
4. Common Mistakes When Applying OWASP
Although OWASP resources are an effective guide for building secure systems, many individuals and organizations still make serious mistakes during implementation. Here are the most common errors:
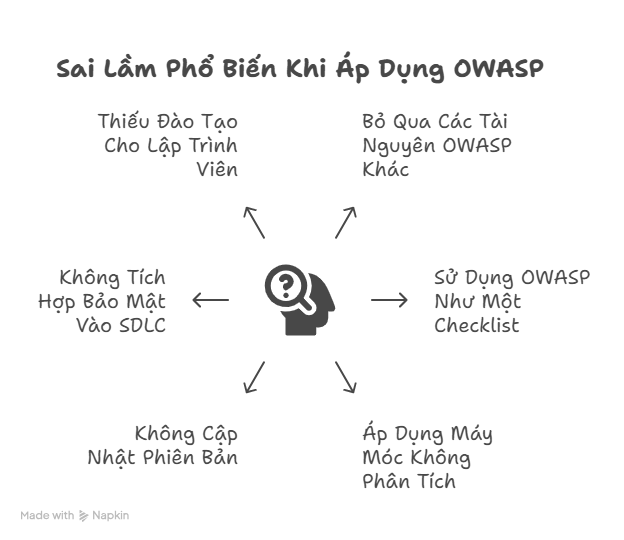
1. Focusing only on the Top 10 and neglecting other OWASP projects
- Misunderstanding: Many people think that simply protecting against the OWASP Top 10 is enough to ensure security.
- Reality: OWASP provides many resources such as ASVS (Application Security Verification Standard), Security Knowledge Framework, Cheat Sheets Series, etc. — all of which are very useful for building a comprehensive secure system.
- Consequence: Missing out on advanced standards and security-by-design guidance.
2. Using OWASP as a fixed checklist
- Misunderstanding: Some security teams treat the Top 10 as a checklist that must be fully ticked off during testing.
- In Practice: The OWASP Top 10 is a risk-oriented guideline, not a complete checklist for every system.
- Consequence: Potentially overlooking vulnerabilities specific to the architecture, programming language, or industry in use.
3. Applying it mechanically without analyzing actual risks
- Misunderstanding: Some organizations apply OWASP rigidly, without assessing which threats are truly relevant to their system environment.
- In Practice: Effective security must be applied within real-world context, including processed data, target users, and system architecture.
- Consequence: Wasting time patching low-impact vulnerabilities while overlooking potentially serious ones.
4. Failing to update to new versions
- Misunderstanding: Using older OWASP Top 10 versions, such as 2013 or 2017, without updating to the latest 2021 content.
- Reality: OWASP regularly updates its lists in response to technological developments and emerging threats.
- Consequence: Accidentally overlooking new risks such as Software and Data Integrity Failures (added in the 2021 version).
5. Assigning tasks only to the security team without integrating into the development process (SDLC)
- Misunderstanding: Believing that security is solely the responsibility of the security team.
- Reality: OWASP encourages integrating security throughout the entire development process (DevSecOps).
- Consequence: Development teams lack security knowledge, resulting in code that is prone to vulnerabilities.
6. Lack of training for developers
- Misunderstanding: Assuming that having automated scanning tools is sufficient.
- In Practice: OWASP provides a wide range of specialized training materials for developers (e.g., OWASP Juice Shop, Cheat Sheets).
- Consequence: Developers repeat the same mistakes because they do not fully understand the root cause.
5. Conclusion
Web application security is no longer optional—it has become a mandatory requirement in the digital era, where every transaction, piece of data, and workflow depends on online environments. Just a single vulnerability can lead to serious consequences such as customer data leakage, service disruption, or loss of brand reputation.
Through the OWASP (Open Web Application Security Project) organization and the OWASP Top 10 list, developers, security professionals, and businesses can identify, assess, and prioritize remediation of the most common security risks in web applications. This is not just a warning list—it serves as a guideline for building a secure software development culture, following the principle of Security by Design, which emphasizes implementing security from the design and coding phases.
Understanding, staying up to date with, and applying OWASP standards and resources (such as ASVS, Testing Guide, Cheat Sheet Series, or OWASP ZAP) enable development teams to strengthen their defense capabilities, minimize incident response costs, and comprehensively protect user data. More importantly, this demonstrates professionalism, responsibility, and long-term vision in building sustainable, secure, and reliable technology products.
6. References
[1] OWASP Foundation, “OWASP Official Website.” [Online]. Available: https://owasp.org. [Accessed: Oct. 22, 2025].
[2] OWASP Foundation, “OWASP Top 10 – The Ten Most Critical Web Application Security Risks.” [Online]. Available: https://owasp.org/Top10/. [Accessed: Oct. 22, 2025].
[3] OWASP Foundation, “OWASP Web Security Testing Guide.” [Online]. Available: https://owasp.org/www-project-web-security-testing-guide/. [Accessed: Oct. 22, 2025].
[4] OWASP Foundation, “OWASP Application Security Verification Standard (ASVS).” [Online]. Available: https://owasp.org/www-project-application-security-verification-standard/. [Accessed: Oct. 22, 2025].
[5] OWASP Foundation, “OWASP Cheat Sheet Series.” [Online]. Available: https://cheatsheetseries.owasp.org/. [Accessed: Oct. 22, 2025].
[6] OpenDev, “kienthucmo.com.” [Online]. Available: https://kienthucmo.com/. [Accessed: Oct. 22, 2025].
[7] OpenDev, “kienthucmo.com – Information Security.” [Online]. Available: https://kienthucmo.com/vi/cong-nghe-thong-tin/an-toan-thong-tin/. [Accessed: Oct. 22, 2025].
[8] OpenDev, “kienthucmo.com – OWASP.” [Online]. Available: https://kienthucmo.com/tag/owasp/. [Accessed: Oct. 22, 2025].